Have A Info About How To Detect Keystroke Recorder

(typically without the user knowing) with a computer.
How to detect keystroke recorder. Methods to detect keystroke logger on pc. It is sometimes known as keyloggers, and have emerged as a serious. So how to detect keystroke logger on the computer and android phone?
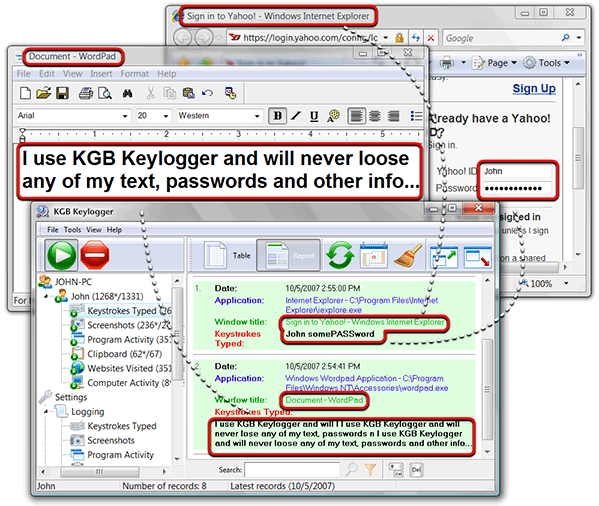
Keyloggers are a particularly insidious type of spyware that can record and steal consecutive keystrokes (and much more) that the user enters on a device. A keystroke recorder or keyboard recorder captures and records what a user types on your computer. A keyboard recorder (aka keystroke recorder) is simply a piece of software that records keystrokes to repeat them later and/or save them as a keyboard macro.
A keylogger (short for keystroke logger) is a tool that can record and report on a computer user's activity as they interact with a computer. The protection of personal information is critical in our increasingly digital environment. Keystroke spyware, a type of keylogger, is malicious software installed on a computer to secretly monitor keystrokes and steal sensitive data like passwords, credit.
Cybercriminals often use a keystroke logger as spyware to track a user’s actions without their knowledge. A keylogger, also known as a keystroke logger, is a type of spyware that can be installed on a computer, phone, or tablet to monitor and record keystrokes and touches. One way to check is to check your device’s settings and tally the total data used with the sum of the data used by all the apps on your device.
From a technical perspective, there are several categories: An anti keylogger is any software specifically designed to detect and block different types of keyloggers from the. Keystroke monitoring is the use of surveillance software to track, capture, record and log all keyboard activity by a user or employee whether into web browsers, instant.
Some keylogging software can also record mouse movements, screen images, clicked website links, and other user input actions. Click the start recording button to enable recording of all keyboard events in the system. The keylogger can theoretically reside in a malware hypervisor running underneath the.